Best Of
10 Best Open Source Intelligence (OSINT) Tools

Open source intelligence (OSINT) software is becoming an increasingly important tool for gathering public information. This type of software allows users to gather easily accessible data on individuals and organizations from a wide range of sources — such as search engines, social media profiles, and government records — with the aim of creating a comprehensive picture.
Advanced OSINT software can then cross-reference this data to provide an accurate source of knowledge and build connections between different pieces of information that may otherwise have gone unnoticed. In today’s data-driven world, OSINT software provides an indispensable resource for anyone looking to gain insight into themselves or those around them. It has also become increasingly popular for cybersecurity professionals using it for ethical hacking, penetration testing and external threat identification.
OSINT is a key component of Open-Source Business Intelligence (OSBI), a meta trend that is rapidly growing. OSINT eliminates the hefty associated cost which can be prohibitive for smaller businesses, and it has emerged as an attractive model of BI due to its lower cost and scalability. Currently, around 26% of companies use open-source tools as part of their business strategy and this number is likely to grow significantly in the future.
The OSINT market is expected to experience significant growth over the next five years–providing ample opportunity for startups looking to break into this space.
Here are some some of the best open source intelligence tools on the market:
1. Maltego
Maltego is a versatile open source intelligence platform that can simplify and expedite investigations. It provides access to 58 data sources and manual upload capabilities, as well as databases of up to 1 million entities to help you conduct better analysis. Its powerful visualization tools also enable you to choose from different layouts like blocks, hierarchical, or circular graphs with weights and notes for further refinement.
With Maltego, trust and safety teams, law enforcement personnel and cybersecurity professionals get one-click investigation results with easy-to-follow insights.
OSINT can be invaluable in a variety of sectors, from law enforcement to financial services. This is why the company also invests heavily in providing fantastic resources on OSINT tools and techniques. Not only are these varied and comprehensive, they’re also hand-picked by an expert team to ensure customers get the very best out of their product. The company also offers a Maltego Foundation course available for purchase online.
2. Spiderfoot
Spiderfoot is an open-source OSINT reconnaissance tool with a variety of features, including the ability to obtain and analyze IP addresses, CIDR ranges, domains and subdomains, ASNs, email addresses, phone numbers, names and usernames, BTC addresses, and more.
Offering both a command-line interface as well as an embedded web-server equipped with a user-friendly GUI interface which is accessible on GitHub, Spiderfoot boasts over 200 modules which can be used to carry out the most comprehensive activities and uncover key details about any target.
It can also be used to assess whether or not organizations have data exposed that could potentially cause security breaches. All in all, it is a powerful cyber intelligence tool capable of providing invaluable insights into potentially harmful online entities.
3. OSINT Framework
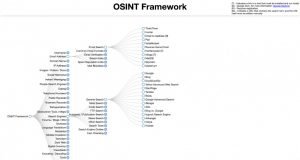
OSINT Framework is a great resource for open-source intelligence gathering. It has everything from data sources to helpful links to effective tools, making it much easier than trying to individually research every program and tool out there.
This directory also provides options for operating systems beyond Linux, providing solutions across the board. The only challenge may be developing an effective search strategy that narrows down results such as vehicle registration or email addresses, but with such organized resources, this ends up being more of an asset than ever.
The OSINT Framework is quickly becoming one of the most popular solutions for data collection, information discovery and sorting things out.
4. SEON
In today’s digital economy, verifying someone’s identity using various social media and online platform accounts as data points is becoming more commonplace. SEON is at the forefront of this digital identity verification movement.
By tapping into its email and phone number systems, your business can access over 50 different social signals that produce a comprehensive risk score. These signals not only confirm the validity of a customer’s email address or phone number but also collect deeper insights regarding their digital footprint.
Furthermore, SEON provides businesses with the flexibility to implement queries manually, via API, or even through a Google Chrome extension; making it easier to use and accessible.
5. Lampyre
Lampyre is a paid application designed specifically for OSINT, providing an efficient solution for due diligence, cyber threat intelligence, crime analysis, and financial analytics. It is an intuitive, one-click application that can be installed on your PC or run online with ease.
Starting with a single data point such as a company registration number, full name, or phone number, Lampyre automatically processes 100+ regularly updated data sources to reveal useful information.
If needed, you can access the data via PC software or through API calls. For businesses looking for a comprehensive platform to monitor risks and investigate threats of various kinds, Lampyre’s SaaS product offering – known as Lighthouse – allows users to pay per API call.
6. Shodan
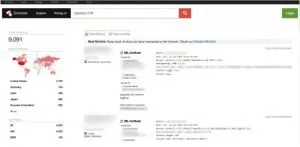
Shodan is an advanced search engine that allows users to quickly identify and access information on the technology used by any business. By typing in a company name, one can receive detailed insights into their IoT devices – such as location, configuration details and vulnerabilities – grouped according to network or IP address.
Additionally, employers may use Shodan for further analysis of operating systems being used; open ports; web server type and design language employed with high accuracy achieved through its cutting-edge software toolsets.
7. Recon-ng
Recon-ng is a powerful tool used to find information related to website domains. It originally started as a script, but now it has evolved into a full framework.
When using Recon-ng, users are able to identify web vulnerabilities including GeoIP lookup, DNS lookup, and port scanning. It is extremely useful for locating sensitive files such as robots.txt, finding hidden subdomains, looking for SQL errors, and retrieving company CMS or WHOIS information.
Despite being more technical in nature compared to other tools available on the market, there are many helpful resources available that you can use to learn how to take full advantage of this top software.
8. Aircrack-ng

Aircrack-ng is a powerful and comprehensive security penetration testing tool used by digital security professionals to test the safety of wireless networks. The tool enables users to collect information related to packet monitoring, including capturing of frames and collecting WEP IVs along with the position of access points if a GPS is added.
It can also conduct penetration tests on networks and analyze the performance by token injection attacks, fake access points and replay attacks. Finally, it can perform password cracking for both WEP and WPA PSK (WPA 1 and 2). Aircrack-ng represents an indispensable tool for assessing the potential vulnerabilities in a wireless network before they can be potentially exploited.
The versatility of this tool is a major highlight; it was developed primarily for Linux but can be adapted to other systems such as Windows, OS X and FreeBSD. Furthermore, its capability as a command line interface (CLI) gives it an edge in customization. This means that more advanced users can easily create custom scripts in order to further modify the tool and tailor it to their unique requirements.
9. BuiltWith

BuiltWith is an incredibly powerful website detective, allowing users to find out the tech stack, frameworks, plugins, and other information powering popular websites. This can be useful for those interested in using similar technologies for their own sites.
Additionally, BuiltWith also lists JavaScript/CSS libraries that a website may be using, providing further granularity and insight into the architecture of certain websites. As a result, BuiltWith is not only useful for casual research but can also be used to conduct reconnaissance on behalf of businesses or organizations who need to know precisely how different webpages are put together.
For added security assurance, you can combine BuiltWith with website security scanners like WPScan that specialize in identifying common vulnerabilities impacting a website.
10. Metagoofil

Metagoofil is a freely available tool on GitHub which specializes in extracting metadata from a variety of public documents, including .pdf, .doc, .ppt and .xls. As an incredibly powerful search engine, it is able to unearth useful data such as usernames and real names associated with specific public documents, along with server information and the path to these documents.
While this information presents significant risks to organizations, the same data can also be leveraged as a defense mechanism. Organizations can take proactive steps to ensure that the information itself is hidden or obscured before malicious actors have an opportunity to use it for ill means.
Summary
Open Source Intelligence (OSINT) software is becoming an essential tool for collecting public information from diverse sources like search engines, social media, and government records. By leveraging advanced algorithms, OSINT tools can cross-reference and analyze data to provide accurate insights and uncover hidden connections. This technology is invaluable for cybersecurity professionals, law enforcement, and businesses seeking to gain comprehensive knowledge about individuals or organizations. As OSINT continues to grow, its cost-effectiveness and scalability make it an attractive option for companies aiming to enhance their business intelligence strategies.










